Forgepoint Forward Q2 2025: What’s Ahead in Security Log Data Management
Preisha Agarwal, Rey Kirton
April 30, 2025
- Blog Post

Forgepoint Capital is excited to announce the third edition of Forgepoint Forward for Q2 2025: What’s ahead in Security Log Data Management.
About Forgepoint Forward
Forgepoint Forward is a quarterly series that aims to uncover emerging opportunities for innovation and investment while spotlighting the startup landscape. Created for entrepreneurs, information security leaders, and the broader information technology community, each report combines extensive primary and secondary market research along with expert opinions and insights from our community of CISOs, CEOs, executives, and Global Advisory Council members.
Key Insights
The third installment in this series delves into the state of the emerging Security Log Data Management (SLDM) market, with analysis and perspectives from the Forgepoint portfolio and beyond.
Persistent log data management challenges
Security logs timestamp security events, system changes, and user access, providing foundational data to enable effective detection, correlation, response, and compliance functions. As log data sources and volumes have increased, Security Operations Center (SOC) teams face persistent data management challenges. Our analysis found four recurring issues:
- Exponential Log Growth Presents a Data Storage Dilemma: Security teams are facing an unprecedented volume of security logs generated across increasingly complex IT and cloud environments. The growing demand for faster and more advanced security log analytics at scale presents a dilemma: whether to send log data to higher cost, security-focused SIEMS for correlation and analysis or to more generalized and cost-efficient data lakes for cold storage.
- Skyrocketing SIEM Costs: Rising costs around SIEM licensing and installation, infrastructure demands, and SOC staffing are forcing organizations to make tough tradeoffs. Companies facing limited budgets must resort to filtering or excluding log data sent to SIEMs- often at the expense of detection and visibility.
- Vendor Lock-In: Most SIEMs are inflexible and difficult to rip and replace. Enterprises often choose to seek an additional log management solution instead- which must integrate with their current SIEM’s restrictive architecture.
- Technical Analysis Requirements: SIEM-level security analysis requires highly technical and often vendor-specific programming skills, a tall order given the industry-wide skills shortage and mounting alert fatigue among short-staffed SOCs.
Here’s what our community of security experts and practitioners had to say about current log data management challenges:
-
“The architecture has collapsed: the ecosystem utilizes 18 different tools and costs hundreds of dollars per GB. How will you start to automate or improve the decision-making capabilities of a human when you’re dealing with billions of events? Something must change: a disruptor needs to come in because the market is broken.”
 George Webster CEO - Ziggiz
George Webster CEO - Ziggiz -
“The cost for cyber logs sent to the SIEM can be 10x higher than the cost in the retention realm, where the operational or business intelligence log is simply retained for auditors and not analyzed for security benefit.”
 David Emerson CTO - SolCyber
David Emerson CTO - SolCyber -
“The effort to move SIEMs at a 5,000-person enterprise takes multiple years and millions of dollars. This amount of spent time and money for moderate cost savings does not make sense– the SIEM is a very difficult product to pull out [and replace].”
 Ramin Safai CISO - Point 72 Ventures
Ramin Safai CISO - Point 72 Ventures
SLDM market opportunities
SLDM providers have an opportunity to address these challenges with intermediary routing platforms that effectively ingest, aggregate, enrich, and transfer log data from numerous sources. These solutions have the potential to provide three key benefits:
- Cost Efficiency: SLDM solutions which correlate log data and offer flexible routing rules to control the volume of data sent to SIEMs versus cold storage- without sacrificing visibility and security posture- can help enterprises circumvent unsustainable costs.
- Faster and More Accessible Data Analysis: SLDM solutions with capabilities including abstracted pipeline and routing configurations and recommendations, telemetry normalization, and real-time data lookups can help streamline the log data analysis process.
“The externalization of configuration is beneficial– it serves as an abstraction layer. You can now make security-focused decisions about what is being routed into security infrastructure. It is simpler and more delegable for the security team.”
 David Emerson CTO - SolCyber
David Emerson CTO - SolCyber
- Enhanced UI and UX: Security analysts need more practical ways to view log data, prioritize queries, and intelligently route logs. SLDM tools that offer high-level data visualizations and do not require highly technical skills will be in high demand.
SLDM market map
Through our research, we mapped the existing SLDM market across two dimensions- commercial focus (general vs. security) and target functionality (low-code vs. custom pipeline creation):
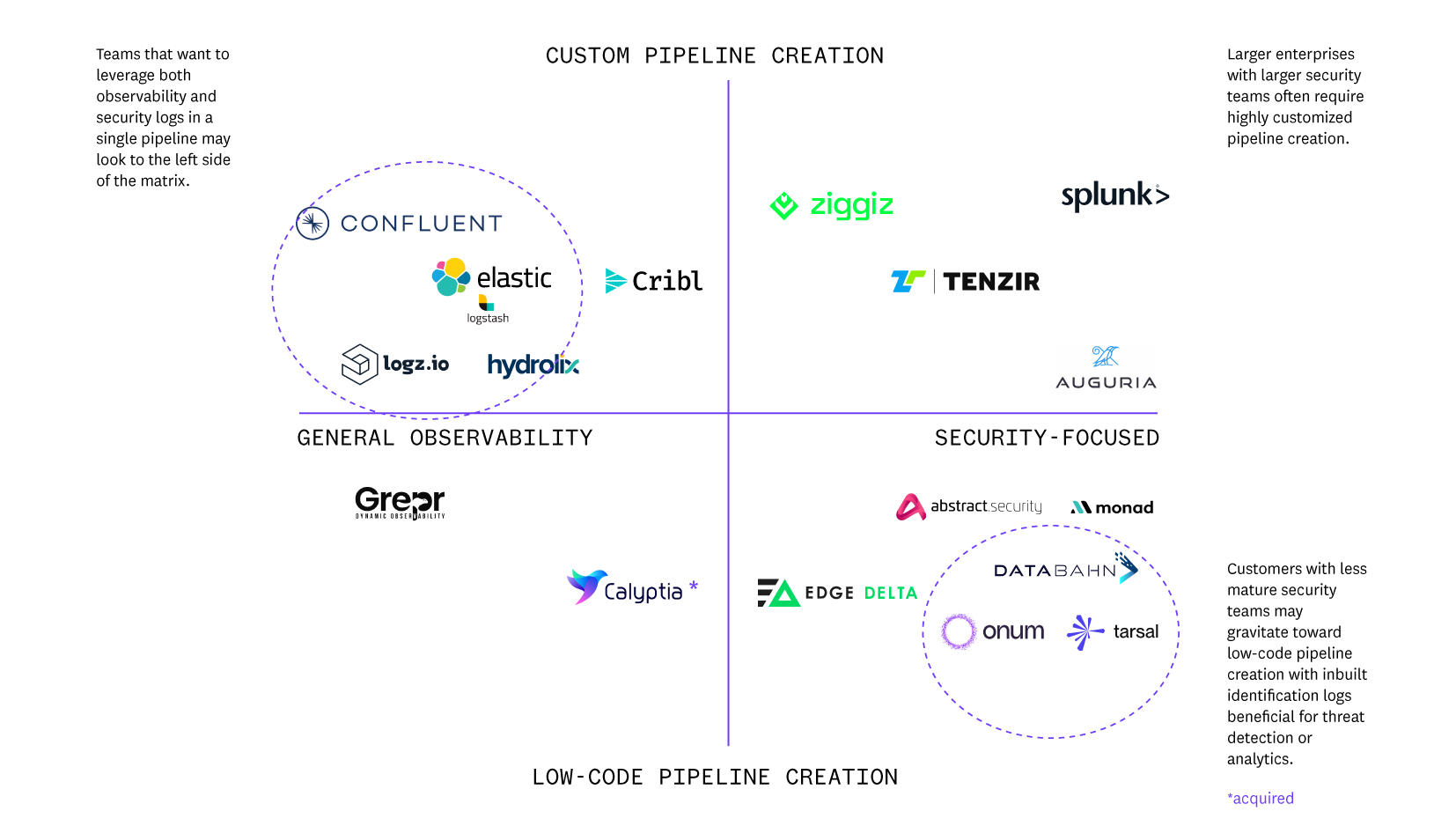
Large enterprise buyers with more resources to code pipelines requiring highly specific routing schema may look to the top two quadrants for custom solutions. Enterprises with security-focused log management needs will likely gravitate towards the top right quadrant (Splunk (acq. Cisco), Tenzir, Ziggiz) while those developing a unified pipeline for both general and security observability may look to the top left quadrant (Cribl, Confluent, Elastic).
Down-market buyers with more limited security resources may find more value in low and no-code solutions which offer built-in guidance around log routing- those in the bottom two quadrants (Grepr, Databahn, Onum).
Market Dynamics and Trends
Our research identified three dominant market trends defining the SLDM space:
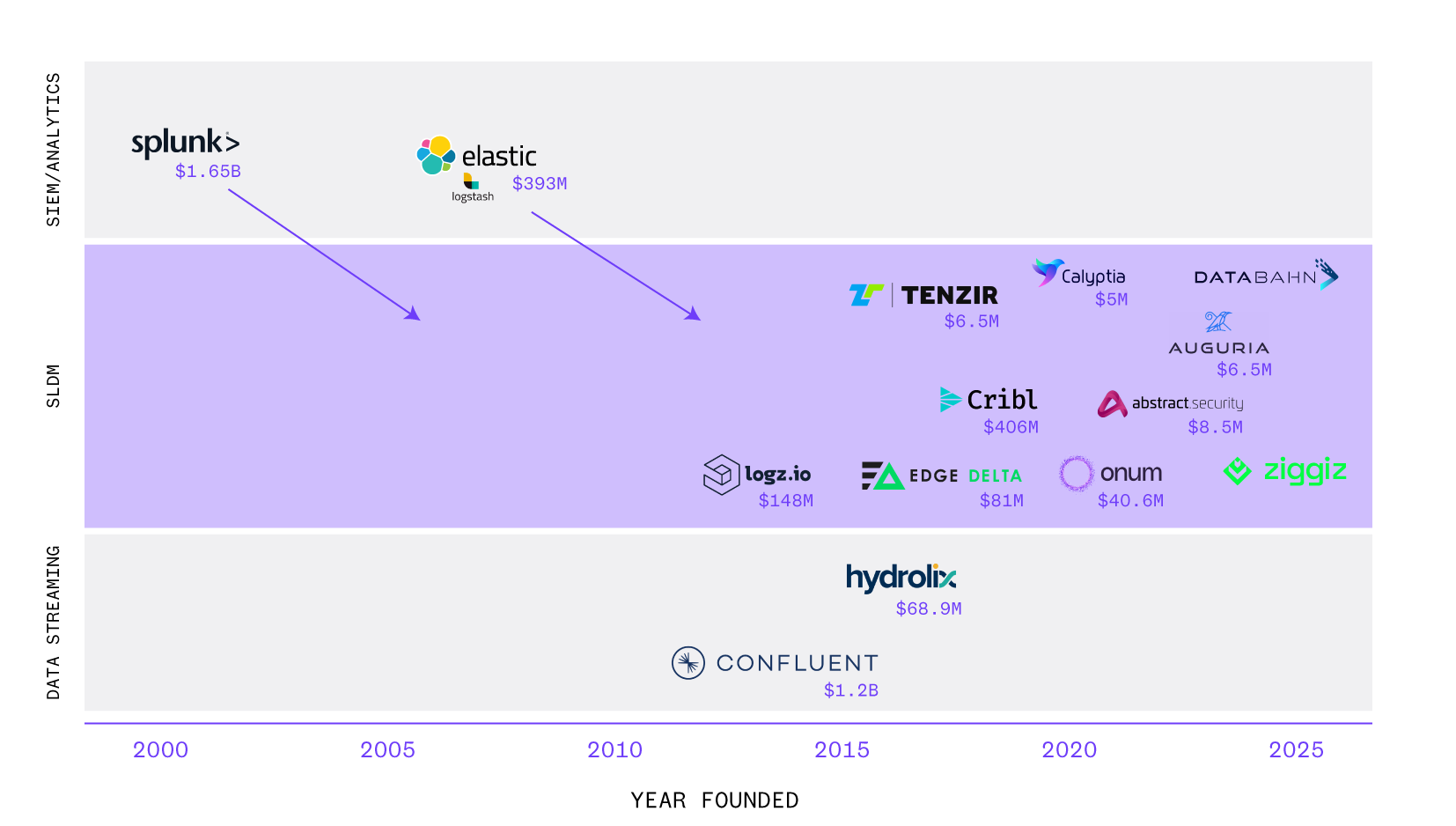
- Overlap between SIEM and SLDM Product Roadmaps: Some SLDM players (Edge Delta, Hydrolix, Cribl) have gained significant mindshare by offering flexible, cost-efficient data storage alternatives to legacy SIEMS. At the same time, legacy SIEM providers (Splunk, Elastic, Confluent) have started to enter the SLDM space, offering SLDM capabilities at a discount and adapting their licensing models to address cost concerns. This convergence has the potential to stifle newer SLDM market entrants, who must now provide capabilities beyond log filtering alone. Enterprise SLDM adoption remains uneven, and it remains to be seen if SLDM startups can displace legacy SIEM vendors. It’s also possible that larger enterprises may wish to utilize both- legacy SIEMs for storage and an SLDM solution at the pipeline.
“Large companies often have years of investment in Splunk. Displacement is possible, but it is going to be expensive from a time investment perspective. It requires two platforms to run at the same time- use cases have to be moved over to a new platform one at a time.”
 Jerry Kowalski CISO - Jefferies
Jerry Kowalski CISO - Jefferies
- Cribl is Dominant among Entrants: Cribl, valued at $3.5B, has a commanding lead over other SLDM entrants in market share, mindshare, and funding. However, there are some concerns around its licensing model and potential price increases. Ultimately, Cribl’s generalized focus and custom capabilities likely leave room for security-focused and low or no-code startups to find momentum.
- Unmet Needs among Mid-Market and SMB Buyers: Mid-market buyers may gain the most from platforms that deliver cost savings, faster analytics, usability, and in-built security guidance. With smaller budgets and SOCs than enterprises, these buyers often find SIEMs prohibitively expensive; there’s a significant opportunity for SLDM providers to meet mid-market user needs. While VC funding has been largely concentrated on market leaders serving enterprises, we expect more investment in startups that capitalize on the mid-market. For SMBs, the name of the game is plug-and-play solutions that solve log collection and log traffic problems. SLDM providers that offer simple, cost-effective solutions may find a large untapped pool of SMB buyers.
“From working with hundreds of thousands of SMBs and the MSPs who serve them, it became obvious the industry needed a better SIEM solution that eliminates unnecessary data and alerts, streamlines complexity, and cuts out unpredictable costs. In this era of mounting threats and vulnerabilities, focus is everything: on just the data you need, paying only for what you’ve used.”
 Chris Bisnett CTO and Co-Founder - Huntress
Chris Bisnett CTO and Co-Founder - Huntress
Looking ahead at next-gen SLDM solutions
As legacy SIEM providers enter the SLDM space via acquisitions and SLDM players begin to build out SIEM-like hot storage capabilities, what will set SLDM solutions apart from the crowd? Based on our analysis and conversations with security leaders at the front lines, we believe vendors offering data normalization, intelligent routing schema, and AI-powered log analysis are well positioned to succeed:
- Pipeline solutions formatting data in common standards like OCSF or OTel have the potential to automate and optimize data management processes which are currently linear, fragile, and expensive.
- Data routing- whether it occurs via predefined schema or customizable pipelines- must add intelligent context while keeping humans in the loop to enable more flexible and effective data analysis.
- AI-enabled capabilities have the potential to reduce latency across the entire SLDM workflow, including data normalization, processing, routing, detection, correlation, and analysis.
Here’s what our community of security leaders are looking for from the next generation of log data management solutions:
-
“Standards like OTel and OCSF provide a certain comfort level that you can change tools- or have ten tools- because you have a standard way of collecting data.”
 Jerry Kowalski CISO - Jefferies
Jerry Kowalski CISO - Jefferies -
“You must have data in a form where you eventually have a human investigation because you do not know the process and the method of an attacker. It is not as simple as ignoring logs by dropping them in cold storage to reduce log growth. If you don’t have a system that allows flexibility or agility, none of that important information is being processed or collected for analysis.”
 George Webster CEO - Ziggiz
George Webster CEO - Ziggiz -
“The difficulty we face is to control the data quality; the performance indicators related to that are the most relevant [to selecting a SLDM solution]. The analyst who has to interpret the data system often does so in near-real time, not real-time. Thousands of alerts may not be reviewed, and for low-urgency alerts there can be minutes or hours between detection and analysis.”
 Joaquin Sanchez Iglesias Security Monitoring & Analytics - Santander
Joaquin Sanchez Iglesias Security Monitoring & Analytics - Santander
Are we bullish or bearish on SLDM?
Read our full report to find out:
- What industry-leading CISOs, executives, and experts have to say about persistent log management issues and compelling SLDM solutions
- How SLDM startups can address challenges around logging volume and costs, vendor lock-in, and technical barriers
- Our take on the market (are we bullish or bearish?) and what might change our minds
Download the report here:
Acknowledgements
Thank you to the following security leaders and experts for providing essential insights:
- Chris Bisnett, CTO & Co-Founder, Huntress
- David Emerson, CTO, SolCyber
- Jerry Kowalski, CISO, Jefferies
- Ramin Safai, CISO, Point72 Ventures
- Joaquin Sanchez Iglesias and Guillermo Fuente Diaz, Digital Services, Santander
- Ricardo Villadiego, CEO & Founder, Lumu Technologies
- George Webster, CEO, Ziggiz
For Forgepoint Capital:
Preisha Agarwal, Research Analyst Intern
Rey Kirton, Principal
Ernie Bio, Managing Director
Leo Casusol, Managing Director
Conor Higgins, Marketing Consultant
Tanya Loh, Chief Marketing Officer