Guest Blog: Response under Pressure during a Ransomware Attack
Billy Gouveia, CEO & Founder of Surefire Cyber
December 5, 2024
- Blog Post
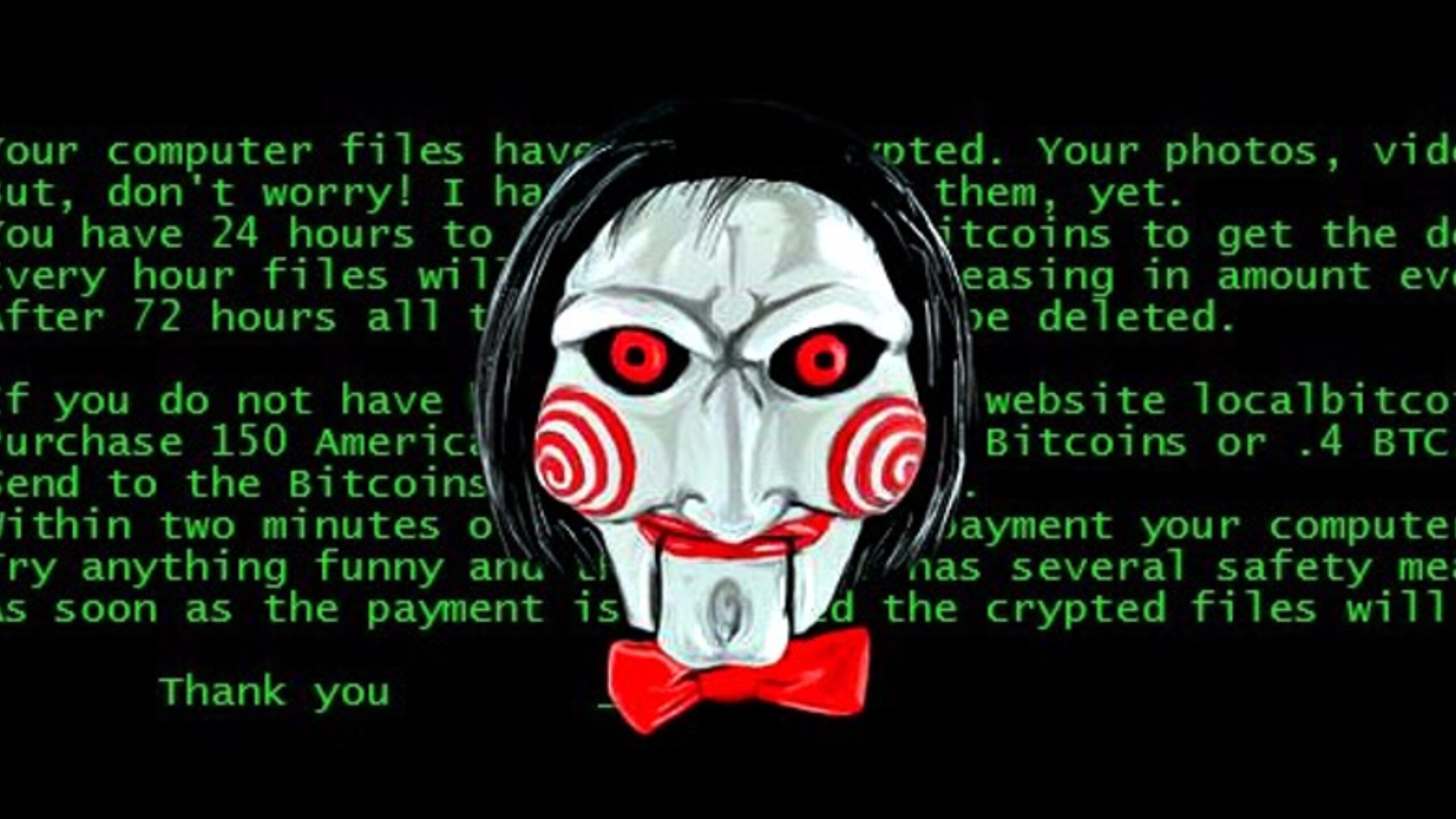
Ransomware attacks pose a significant threat to companies of all sizes and across all industries. As organizations increase their reliance on technology, they often outpace their ability to implement adequate security controls. This creates opportunities for cybercriminals to exploit security gaps and target data, the DNA of modern business.
At a fundamental level, ransomware can be defined in one of three ways:
- A threat actor encrypts data and demands a ransom in exchange for a decryption key.
- A threat actor steals data and demands a ransom in exchange for a promise to not publish the data.
- Both 1 and 2. This is known as double extortion.
What makes ransomware so appealing to threat actors?
Ransomware is the perfect crime. It is easy to commit, enormously lucrative, and done with (near) impunity.
Ransomware threat actors are continually advancing their attack methods, increasing both their sophistication and frequency. This means greater disruptions and increased costs for companies. The impact of a cyber incident is significant, with the average data breach costing $4.88 million globally. Costs stem from many factors including business interruption, forensic analysis, data repair and reconstruction, legal and regulatory fees, ransom payments, and identity remediation services.
To better understand how ransomware works, let’s walk through the six steps that threat actors commonly use and comment on the key defenses and response actions companies should take at each stage.
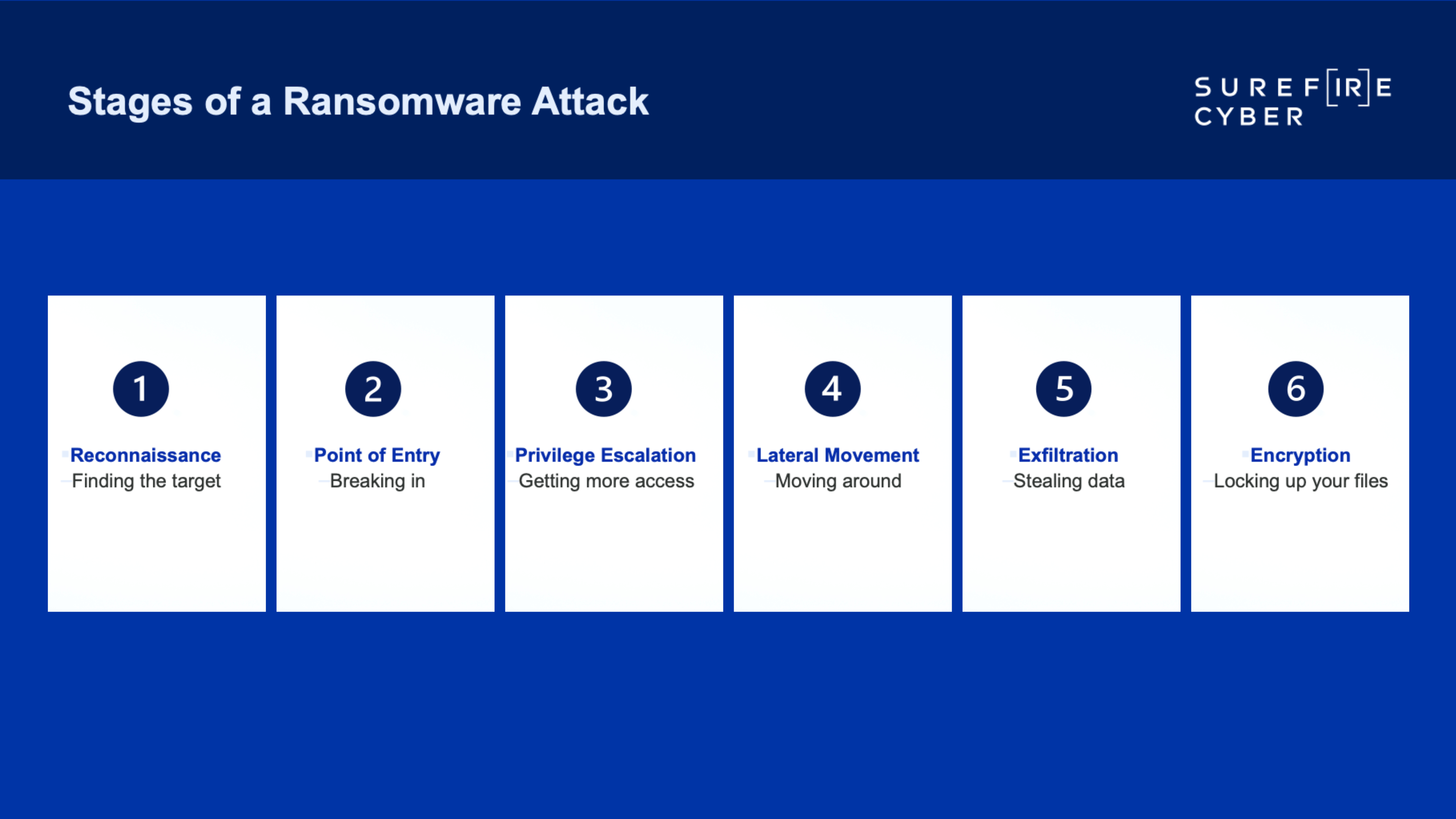
1) Reconnaissance
Threat actors are constantly scanning the internet to find the right target. They are looking for organizations that are exposed to common vulnerabilities. Threat actors can run a full scan of the internet to identify exposure to certain vulnerabilities in as little as 45 minutes.
In other words, you don’t have to be specifically targeted to become a victim. This makes it essential to secure your internet-facing perimeter by closing remote access protocols and enabling multi-factor authentication, as doing so can help prevent ransomware incidents in the first place.
2) Point of Entry
If threat actors don’t find an external weakness, they might instead seek a point of entry to break in. They often send phishing emails embedded with malware to accomplish this goal. Phishing can be generic or targeted depending on the threat actor.
From a security perspective, multi-factor authentication is one of the best ways to prevent a phishing attack. When combined with user awareness training and email filtering, it significantly reduces the risk of a phishing attack. It is also important to implement an Endpoint Detection and Response (EDR) tool to identify and respond to malware on user devices.
2) Privilege Escalation
Once a threat actor has access to a user account, their next goal is to elevate their permission by gaining control of the network administrator’s account.
Companies can prevent privilege escalation by minimizing privileged accounts and administrative access. It’s also important to update and patch systems and invest in tools that detect and stop malicious activity.



4) Lateral Movement
After the threat actor has cracked the administrator’s password and gained privileged access, they move within the company network to seek out critical data, backups, and access usernames and passwords.
Network Detection and Response (NDR) tools will detect malicious network activity and are essential here and to stop attackers in their tracks. It’s also important to use strong and long passwords which are harder to crack, especially for administrator accounts.
5) Exfiltration and Backup Deletion
After obtaining all the necessary credentials, the threat actor seeks out and steals sensitive files. They delete any backups they discover to ensure leverage over the victim company. They may also sell or upload the stolen data to the dark web.
To defend against exfiltration and deletion, companies should not only use a strong backup solution but should also test it frequently. It’s also worth noting that at this stage, a data breach has occurred and may trigger legal obligations- even if files are not taken.
6) Ransomware Execution
Finally, the threat actor lock ups the stolen files. They execute their ransomware as quickly and on as many systems as possible, often doing so at inconvenient times like Friday nights or holidays to increase the chances of a slower security response.
At this stage, disconnect (but don’t power off) encrypted systems to preserve evidence for an investigation. Activate your already established incident response plan and start the process of response and recovery.
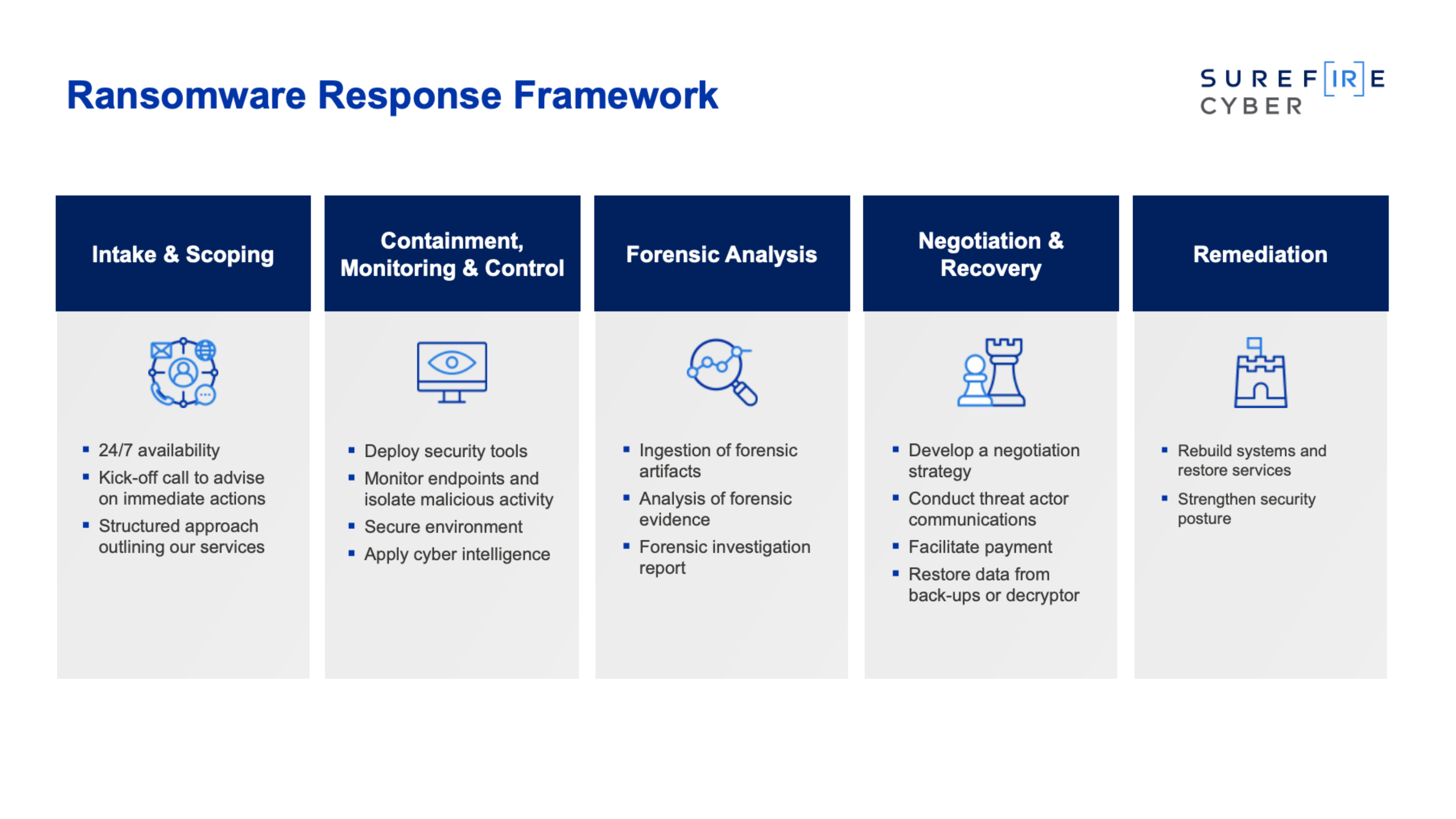
From Response to Resilience
Ransomware is a multidimensional problem involving network intrusion, data theft and business interruption, ultimately leading to legal, regulatory, and reputational risks for an organization. Preparedness, communication, and collaboration are essential to minimize the impact of a ransomware incident and restore operations.
At Surefire Cyber, we are redefining incident response by combining critical thinking and workflow automation to deliver swifter, stronger and more efficient outcomes to cyber incidents such as ransomware, email compromise, malware, data theft and other threats. We provide our clients the confidence needed to help them prepare for, respond to, and recover from cyber incidents, and to fortify their cyber resilience after an event. Visit our website to learn more.
Many thanks to Billy Gouveia, CEO and Founder of leading incident response firm Surefire Cyber, for this guest blog based on his presentation The Anatomy of a Ransomware Attack at our Fall 2024 Advisory Council Meeting.