TIPS #10: Security posture and health: how can companies effectively manage risk and protect themselves from cyber threats?
Shane Shook
November 7, 2023
- Blog Post
- TIPS

Issue: Many companies misevaluate the technology and systems they depend on and adopt inefficient security controls.
The modern enterprise relies upon numerous applications, software, and platforms to drive critical business functions like product development, sales, finance, and IT. However, many companies lack visibility around which tools they use and how they use them across those key functions. As a result, the cybersecurity measures they implement are misaligned with their security needs.
Choosing the wrong security capabilities or policies and managing them inefficiently increases risk across the organization. This is reflected in security posture and health.
Security posture is comprised of all cybersecurity policies, tools, and initiatives a company selects to protect the business, across a range of active (preventative) and passive (reactive) defensive measures. For example, security awareness and education, MFA (multi-factor authentication), and VPNs (virtual private networks) are preventative measures; EDR (endpoint detection and response) is both proactive and reactive; and DLP (data loss prevention) is reactive.
Security health is a measure of how those policies, tools, and initiatives address a company’s security needs and how they are managed. This includes incident response effectiveness, how security teams manage threat alerts, and how well security tools protect key business functions.
Impact: Misaligned security posture and poor security health lead to weaker security capabilities, heightened risk, and greater impacts from Attacks, Breaches, and Compromises.
Poor security posture and health are the true ‘insider threat’ for most companies. An ineffective and mismanaged suite of policies, tools, and practices will increase risk and fail to prevent and mitigate Attacks, Breaches, and Compromises. The opportunity for a hacker to enter your systems unchecked or an employee to access resources they shouldn’t is a result of misaligned security posture and poor security health.
A proactive security posture helps your company get ahead of incidents (addressing Attacks and Breaches before they become Compromises) and decreases risk, promoting healthy security practices over the long term. If posture is too passive (reactive), health deteriorates as policies are mismanaged, capabilities diminish, and more Attacks evolve into high-impact Breaches and Compromises.
Good security health promotes an active posture to prevent Breaches and Compromises. For example, efficient incident detection enables faster response and remediation. Poor health tends to push companies towards a more passive posture where they mainly react to incidents and lack the ability to prevent them.
Think of security posture management and health like maintenance for a car. If you drive a car, you rely on its various systems (braking, engine, fuel, transmission, and so on). Your car requires regular maintenance (active posture) like oil changes, brake pad replacement, and tire pressure checks to reduce the risk of a mechanical or electrical failure. You also should attend to warning lights (reactive posture) if there’s an issue with your engine, battery, or transmission. How well you maintain your car affects the health of the vehicle and the likelihood it will break down or become unsafe to drive. You won’t be on the road very long if you never change the oil, ignore the check engine light, or get new tires to fix a problem with the engine. A well-maintained car (good health) will run smoothly for a longer period of time.
Companies should think about security posture management and health in the same manner. Protect the applications, software, and systems you rely on by prioritizing relevant security policies and tools- and managing them effectively.
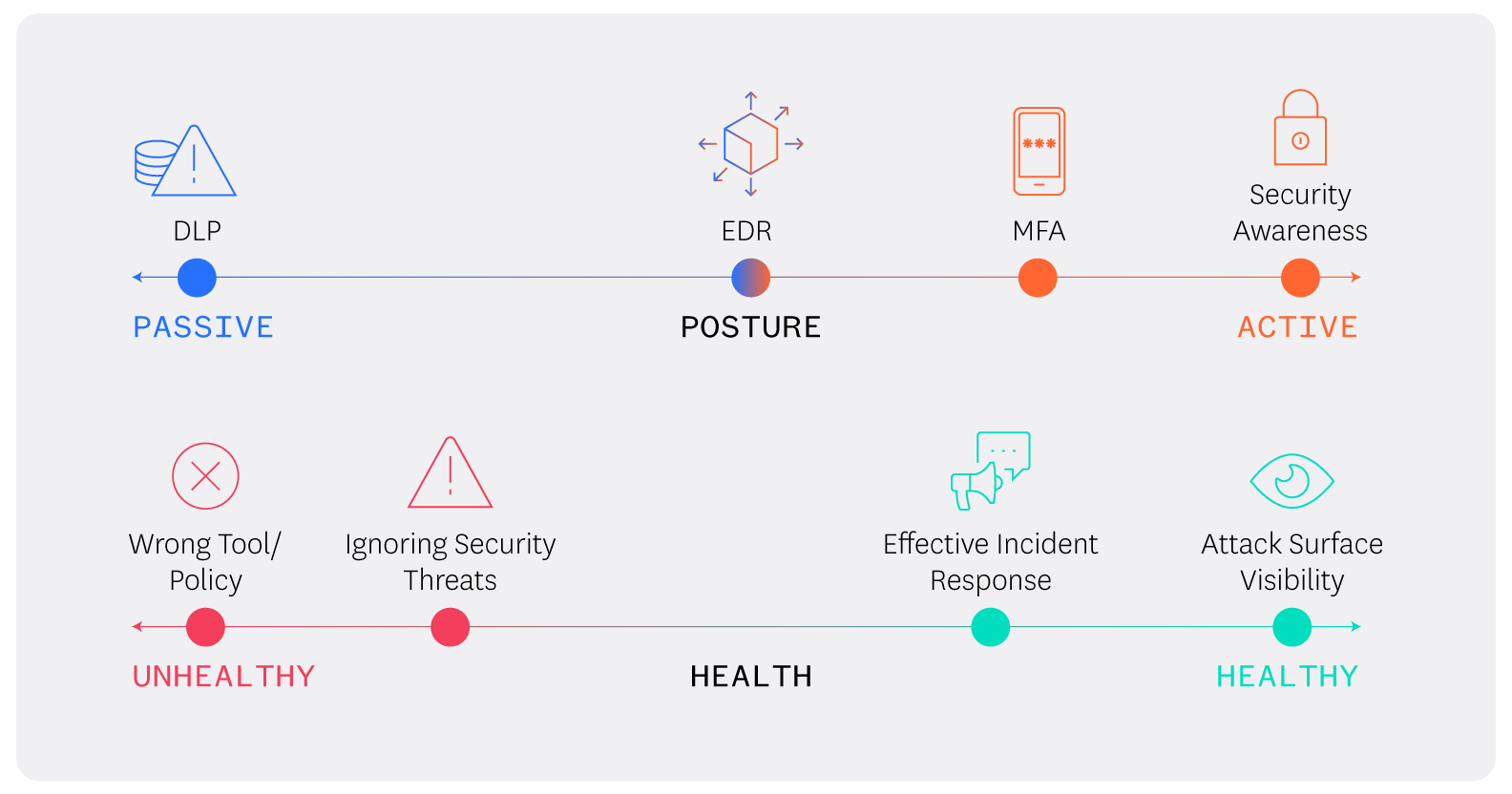
Action: Align your security posture and health to protect key resource dependencies and effectively manage security tools, systems, and policies.
1. Visibility
Identify the technologies and resources your company depends on to run smoothly. Understand which business units are using what technologies and how they are doing so.
Plan around risks to core business functions- this is what attackers are most likely to target. For example, if you are an IT services company, focus on protecting client management access and controls.
2. Security Posture Management
Enable the preventative and reactive capabilities your company needs to protect core business functions. An active posture is critical to prevent Breaches and Compromises. That’s not to say that your company should only use proactive measures (like MFA) and never reactive ones (like DLP). Instead, consider your overall security posture and how well it addresses key resource dependencies. Integrate security policies and tools that meet those needs.
Bishop Fox’s Application Security Posture Management (ASPM) capabilities help you meet external threats with continuous attack surface testing and an active endpoint and perimeter security posture.
SPHERE offers Data Security Posture Management (DSPM) capabilities through SPHEREboard, a platform designed to reduce identity and data risk in your organization.
Uptycs’ Cloud Security Posture Management (CSPM) gives you visibility over resource dependencies and helps you align policies and tools to enable stronger cloud security.
3. Promoting Healthy Security
Fine-tune the management and integration of security policies and tools to prevent, identify, and respond to Attacks, Breaches, and Compromises.
Huntress provides managed endpoint detection and response to help SMBs detect, understand, and respond to cyber threats.
Solcyber helps companies manage a full range of active and passive security capabilities in a unified platform.
Surefire Cyber empowers companies with a comprehensive incident response plan and team.