People, technology, and process issues- misaligned security posture, in other words- have a direct impact on VaR and therefore ROI. The weaker and less aligned a company’s security posture is, the higher their VaR and the more incidents (SOC tickets) they will experience in the later stages of the kill chain (costly breaches and compromises). This lowers ROI.
Conversely, the stronger and more aligned a company’s posture is, the less likely they are to experience a highly impactful incident and the fewer incidents (SOC tickets) they will experience later in the kill chain. This raises ROI.
Similarly, more active security postures will result in more proactive SOC actions (Identify, Prevent, and Defend) whereas more passive security postures result in reactive actions (Respond and Recover).
The takeaway here is that a proactive security posture helps companies detect incidents earlier in the kill chain, reducing VaR and therefore returning a higher ROI from security investments. Security tools, policies, and procedures which support critical business objectives and prevent costly incidents will deliver the best ROI.
Ensure an Active Security Posture with GRC
This is where Governance, Risk, and Compliance (GRC) comes into play. GRC ensures that your security posture is optimized to align with business objectives, meet regulatory requirements (like GDPR and DORA), and manage risks. Strong GRC enables a more active security posture, lowers VaR by helping you detect incidents earlier, and improves ROI by lowering insurance, audit, response, and other costs.
Unfortunately, many companies don’t invest in sufficient GRC to achieve a calibrated and well-aligned security posture. This has a trickle-down effect, raising VaR and leaving them at a greater risk of experiencing impactful and costly incidents.
Impact: Fragmented and inefficient security, decreased security tooling investments, and heightened cyber risks.
Security teams that fail to properly invest in GRC don’t drive ROI across the security stack and are more likely to underinvest in key areas. They typically have poorly coordinated tools which under-protect the business and do not align with key business and regulatory objectives.
This increases the risk of successful attacks, breaches, and compromises, leading to higher recovery costs, greater losses from business disruption, and more regulatory violations. Companies that don’t properly enhance their security posture with GRC are also likely to pay higher cyber insurance premiums than those that do.
To illustrate the impact of insufficient GRC, consider the 2017 Equifax data breach, one of the largest U.S. data breaches on record.
2017 Equifax Data Breach and $575M Settlement
In 2017, credit reporting agency Equifax experienced a massive data breach which exposed personal information including names, Social Security Numbers, and dates of birth for 147 million customers. Equifax’s security team had identified a critical database vulnerability in March and ordered patching within 48 hours, but the company never followed up to patch the systems. In July, the security team detected suspicious network traffic and determined that attackers had exploited the database vulnerability to gain network access before obtaining unsecured admin credentials and stealing the sensitive customer data.
The Federal Trade Commission (FTC) soon filed a complaint alleging that Equifax had failed to secure sensitive customer data and violated the FTC Act’s prohibition against unfair and deceptive practices along with the Gramm-Leach-Bliley Act’s Safeguards Rule. The complaint clarified that the company did not have an effective patching policy, utilized unsegmented database servers, had ineffective intrusion detection systems, and used plain text password storage.
In 2019, Equifax agreed on a settlement of at least $575 million (and up to $700 million) to provide credit monitoring and identity theft services to impacted customers, in addition to making payments to 50 U.S. states and territories along with the Consumer Financial Protection Bureau. The company also agreed to take steps to improve its data security practices, which included annual risk assessments and ongoing security program monitoring and testing.
Action: Leverage GRC to improve security posture management and ensure maximum ROI across your security stack.
1) GRC
GRC is ultimately an efficiency gain. It drives and defines the ROI of a security program by enhancing security posture: the tools, policies, and procedures used to protect the company and its customers. Strong GRC ensures that your investments are selected and deployed to align with business needs and protect key resources.
Hyperproof operationalizes GRC by enabling you to automate workflows, prepare for audits, and mitigate risk in a unified platform.

 Andres Andreu Deputy Chief Information Security Officer, Hearst
Andres Andreu Deputy Chief Information Security Officer, Hearst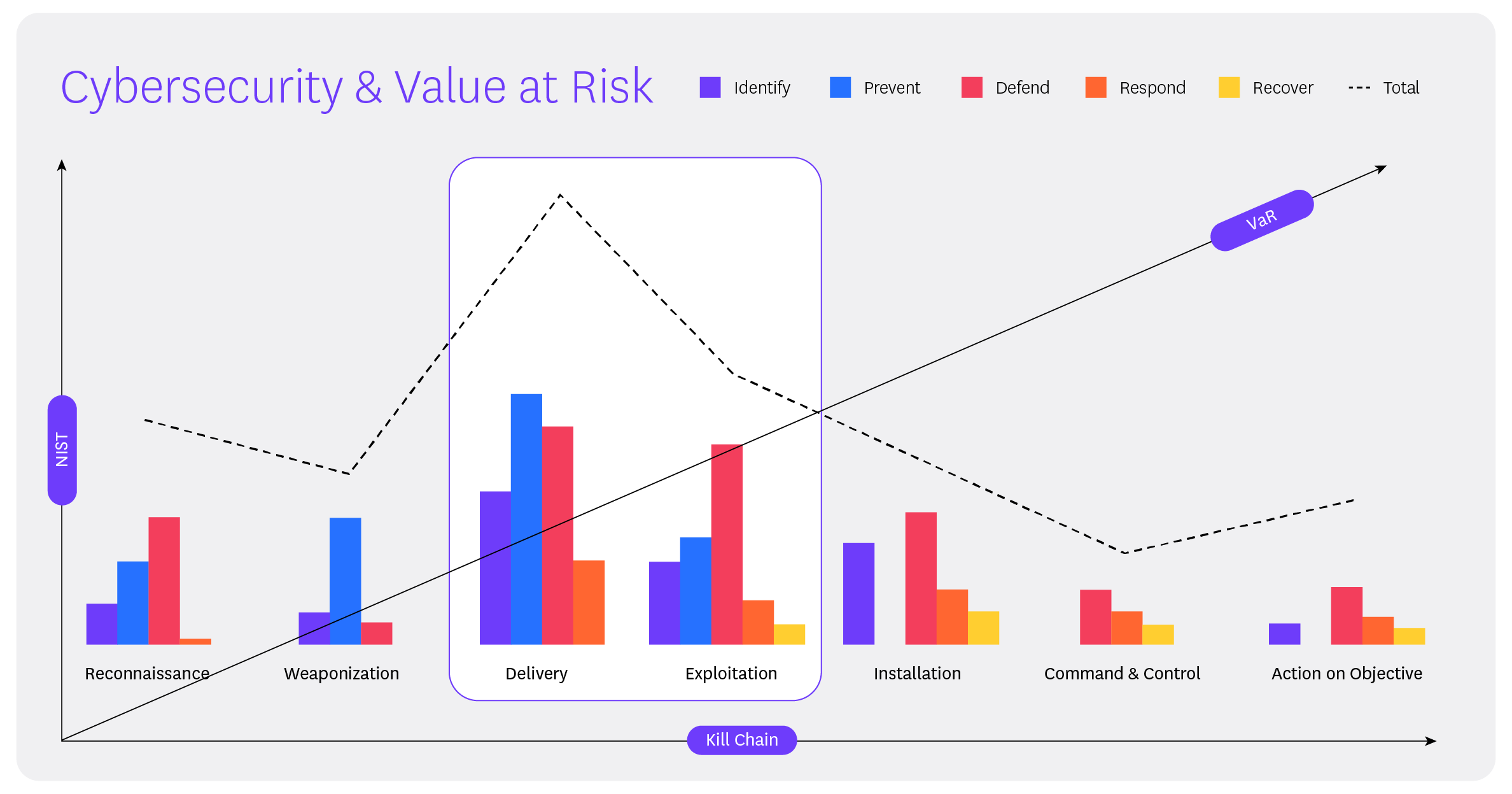
 Craig Unger CEO and Founder, Hyperproof
Craig Unger CEO and Founder, Hyperproof