TIPS #13: How is ITDR Critical to Your Cybersecurity and Governance Strategy?
Shane Shook
January 30, 2024
- Blog Post
- TIPS
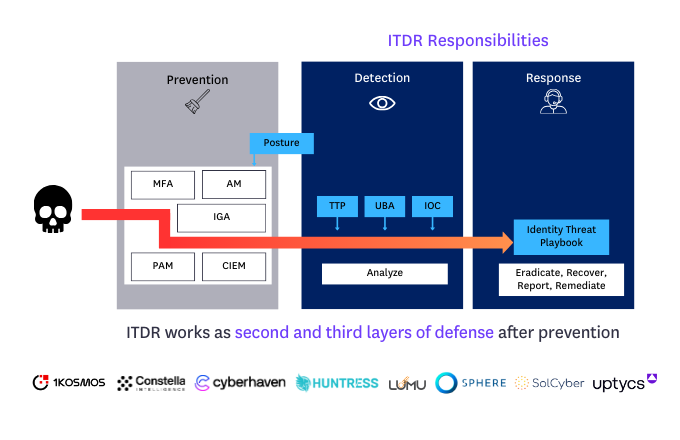
Issue: Cybercriminals increasingly target and compromise identities, but detection and response capabilities are behind the curve.
Imagine: a cybercriminal installs a browser infostealer on a company engineer’s laptop to access 2FA-backed account credentials and browser cookies. They escalate their access to company production systems and steal customer data and encryption keys, compromising sensitive information and secrets stored in code. Some customers experience third-party system breaches as a result.
This is exactly what happened in the CircleCI incident in December 2022.
Identity plays a powerful role in significant cyber incidents today. It is the new perimeter that cybercriminals abuse to access networks, systems, and data. Identity-related attacks like phishing and other forms of social engineering, credential stuffing, and session hijacking are increasingly prevalent. 74% of all breaches involve the human element.
Identity is a critical business asset that needs its own framework for monitoring, detection, and response. Preventative identity measures like IAM, user verification and authentication, and zero trust strategies have become widely adopted. Preventing identity-based incidents is important, but every system can get breached and there are often significant gaps in detection and response that cybercriminals can exploit.
Cybersecurity has traditionally centered on monitoring endpoint and network devices with detection and response playbooks. Unfortunately, companies haven’t adopted the same capabilities for identity across the board.
Impact: Identity-based incidents can have more significant effects than network or endpoint incidents.
In the age of SaaS and cloud services, identity is far more expansive than individual network devices or other endpoints. It translates across enterprise services and third-party partners. As the Circle CI incident demonstrates, a cybercriminal can compromise an entire corporate system with access to a single privileged account.
Identity-based breaches and compromises can have deep and long-lasting effects. Attackers may steal data, install backdoors, move laterally within networks, and deploy ransomware. They increasingly use living-off-the-land techniques to persist and hide their activities. Impacts from identity-based incidents can include system disruptions, data loss or exposure, revenue loss, reputational damage, and other financial and business losses.
Action: Adopt a holistic cybersecurity and governance framework to prevent, monitor, detect, and respond to identity abuse and misuse.
1) Detection and Response
Identity Threat Detection and Response (ITDR) has emerged as a set of identity security tools and practices to complement preventative measures. ITDR capabilities include user behavior monitoring and IAM data collection and analysis. These tools collect information to detect behavioral anomalies, assess risk, and help companies effectively respond to threats.
Uptycs ITDR for Cloud integrates with their extended detection and response (XDR) and cloud detection and response (CDR) capabilities to detect and remediate identity-based threats in the cloud.
Huntress’ Managed Detection and Response for Microsoft 365 protects your company’s Microsoft identities.
Constella Intelligence’s Digital Risk Protection platform helps companies monitor identity exposures, supply chain compromises, and customer account breaches to protect user identities.
Lumu’s Managed Network Detection and Response (NDR) capabilities augment ITDR to highlight compromised identities.
Cyberhaven’s data detection and response and data lineage capabilities protect sensitive data from theft, loss, insider risk, and exfiltration to complement identity security efforts.
2) Preventative Identity Security: IAM, MFA, and more
ITDR works in concert with preventative identity security tools. Leverage Identity and Access Management (IAM) to manage Active Directory (AD) access, Privileged Identity Management (PIM) resource use, and Privileged Access Management (PAM) resource use. Your company should require Multi-Factor Authentication (MFA) and fine-tune it with conditional access rules.
Mobile Device Management (MDM) and Mobile Application Management (MAM) can also complement MFA with conditional access policies to restrict device access.
1Kosmos offers advanced biometric MFA, passwordless enterprise authentication, identity orchestration, and other ITDR-friendly capabilities to secure identities in your organization.
SPHERE identifies and remediates risks related to IAM, PAM, AD, and data management, automating identity security processes.
3) Security posture management
Integrate ITDR in the broader context of your security posture (all policies, tools, and initiatives your company uses). SolCyber helps companies manage their security posture by providing active and passive security capabilities in a unified platform.
*Image from: “Enhance Your Cyberattack Preparedness With Identity Threat Detection and Response” report published 20 October 2022, by Henrique Teixeira, Peter Firstbrook, Ant Allan, and Rebecca Archambault.